Email Authentication: Everything You Need to Know
Casey O'Connor
Email authentication is the process of validating your email messages so that they’re trustworthy and credible enough to pass through the security and spam filters of email service providers (ESPs).
ESPs like Gmail and Outlook need to feel confident that any message they allow into a user’s inbox will not compromise that user’s personal information, passwords, account information, or otherwise violate their privacy. They rely on email authentication to help them know which emails and email senders to trust, and which need to be scrutinized and potentially filtered out.
Email authentication is important for sales teams’ reputations, as well as their overall effectiveness. Even inadvertent mistakes in configuring email authentication can be significantly detrimental to both sender and receiver, so it’s important that sales and marketing teams understand the basics of the process.
In this article, we’ll go over everything you need to know about email authentication, including what it is, how it works, the different types, and why it’s so important.
Here’s what we’ll cover:
- What Is Email Authentication?
- Why Is Email Authentication Important?
- Email Authentication Methods
- How to Authenticate Your Email
- Email Authentication Best Practices
What Is Email Authentication?
 Email authentication is a technical process in which email servers confirm the legitimacy of an email’s sender and its contents.
Email authentication is a technical process in which email servers confirm the legitimacy of an email’s sender and its contents.
Also known as email validation, it’s essentially a way of validating the integrity of an email message. When email authentication is configured correctly, it can prevent fraudulent email activity like spoofing, spamming, phishing, and forging.
In simple terms, email validation helps email recipients feel confident that their incoming messages are being delivered directly from verified, legitimate senders who have no harmful intent.
Email authentication is a digital best practice and a largely assumed expectation for teams that want to promote trustworthiness and transparent, productive communication with their prospects, customers, and colleagues.
Why Is Email Authentication Important?
Over 347 billion emails are sent on a daily basis.
That’s a lot of opportunity for bad actors to try to use your platform (and good reputation) to get the data they’re after.
And with more and more business being done online, we’re only just beginning to understand the broadness and significance of the field of cybersecurity.
Email authentication is one effective way of protecting your email recipients, yourself as a sender, and your messages and their content from malware and bad actors.
There are tons of proven benefits to authenticating your email. 
Protects Your Recipients
Email authentication ensures that those on the receiving end of your email outreach will not be subject to email spammers and scammers.
Without the technical email authentication process, phishers can more easily fool spam filters by changing the source address of email messages so that they appear more legitimate. Ultimately, email authentication helps protect the personal data and overall privacy of those on your outreach lists.
And spam is more than just an annoyance for your email list. It’s a real problem with real financial consequences. Spam costs businesses over $20 billion every year, and over 94% of malware is delivered via email — trust that your recipients are doing whatever they can to avoid associating with anyone with sketchy email practices.
Protects Your Brand
On that note, solid email authentication practices also help portray your brand as one that’s trustworthy, legitimate, and safe to do business with.
It helps solidify your reputation as a business that cares about how it communicates and the impact its outreach has on those around it.
Email authentication also offers email service providers a signal that you pay attention to security requirements and are in compliance with the steps necessary to demonstrate legitimacy.
This, in turn, helps the ESPs receiving your email messages trust that the incoming message is definitely from the real you. This process will help ensure that your overall domain reputation remains intact and free from spam or phishing attacks, which will improve your overall campaign effectiveness.
Ensures Deliverability
Email authentication is a bit like the equivalent of a government-issued ID for ESPs. It legitimizes you and/or your email platform as a trustworthy sender with consistently clean content that’s free of malware.
This makes it much more likely that the IP addresses associated with your email will be trusted by receiving servers. The more trustworthy you are, the more likely it is that your emails will be delivered.
Email authentication is especially important for SaaS companies, given how much their business model relies on ongoing outreach and communication.
Email Authentication Methods
Before we dive into the three primary email authentication methods, let’s take a step back for a very brief and overly simplified explanation of how emails are sent and received.
All email messages are delivered via a system known as SMTP (Simple Mail Transfer Protocol).
This process is actually quite complex, but for the sake of this article, the takeaway is that SMTP does not include any authentication frameworks. All it does is simply deliver messages from one server to another.
Separately, there are three main email authentication frameworks.  The main email authentication frameworks are:
The main email authentication frameworks are:
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM)
- Domain-Based Message Authentication, Reporting, and Conference (DMARC)
All three of these systems rely on the domain name system (DNS), which is essentially like a phone book for the internet.
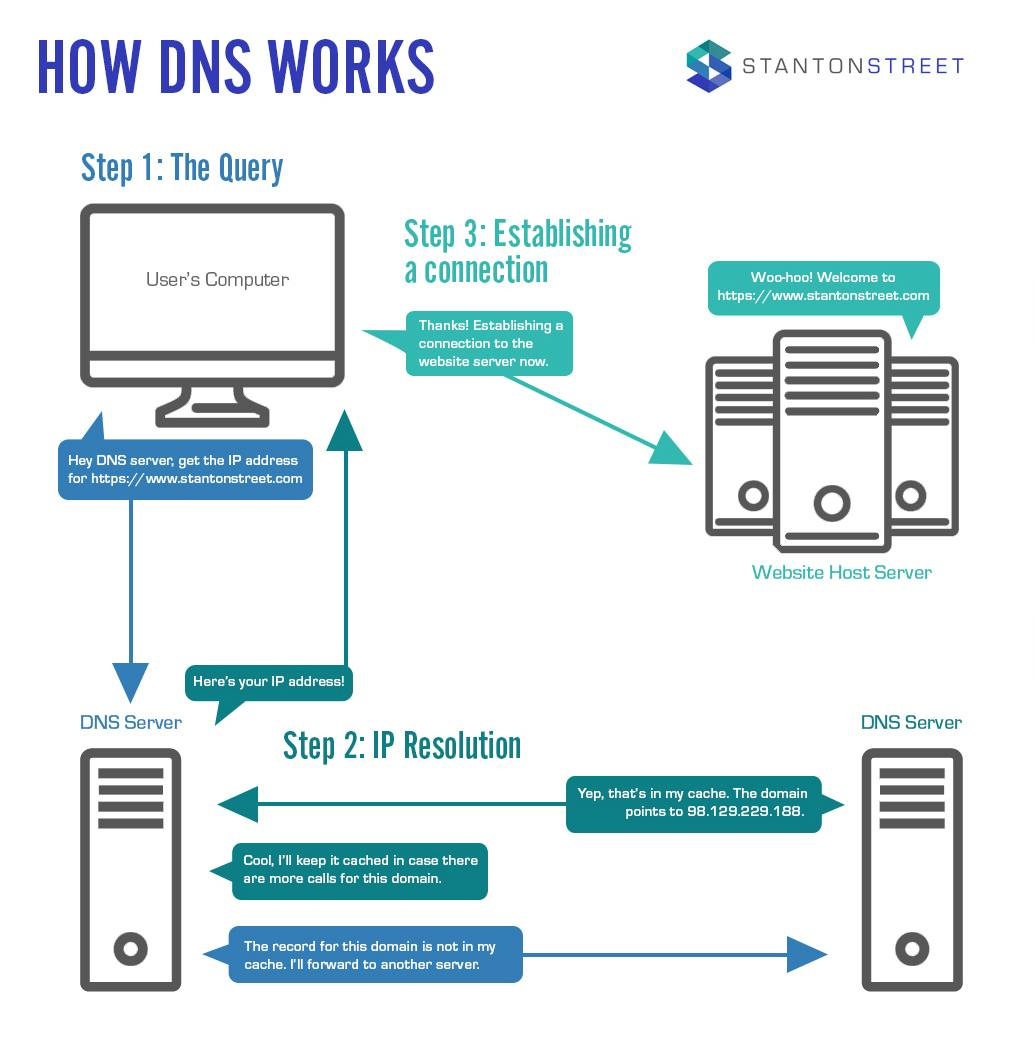
Beyond their interaction with the DNS, however, each of the three main authentication processes functions differently. And, while SPF and/or DKIM are required, DMARC is optional. Most companies find that their email messages are most secure when they use all three.
Sender Policy Framework (SPF)
The Sender Policy Framework (SPF) enables domain owners (i.e., email senders) to create a list of verified IP addresses that have consent to send messages on their behalf.
Recipient email servers then use that list of authenticated IP addresses to cross-check the DNS database when an email arrives in the inbox.
If the incoming IP address matches one from the domain owner’s list, the email is likely legitimate.
If the IP address does not match, however, it’s likely fraudulent. The email server will then have rules to deal with the email accordingly: marked as spam, quarantined for a certain amount of time, or blocked/deleted entirely.
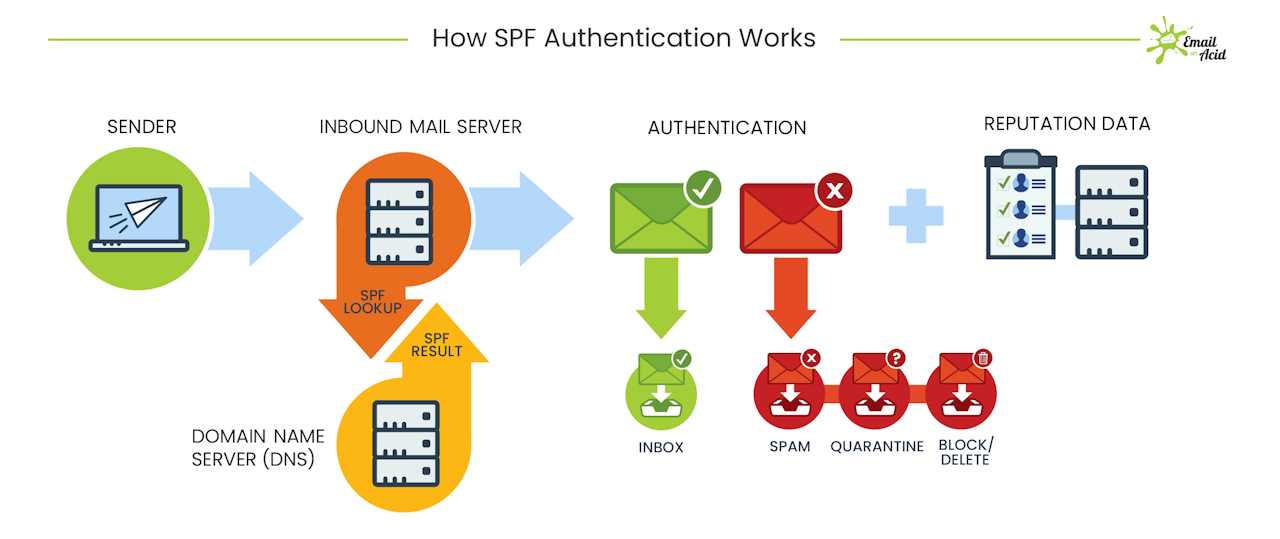
The SPF system helps email servers detect fraudulent senders that attempt to send emails on someone else’s behalf (e.g., spoofing and phishing). It helps verify that the email sender matches their ID, so to speak, and is authentic and trustworthy.
DomainKeys Identified Mail (DKIM)
True to its name, the DKIM system is key-based.
The email sender generates a private and a public key pair. The private key is stored within the sender’s ESP, and the public key is stored in the DNS.
The recipient’s ESP can then verify that your private key matches the key in the public domain.
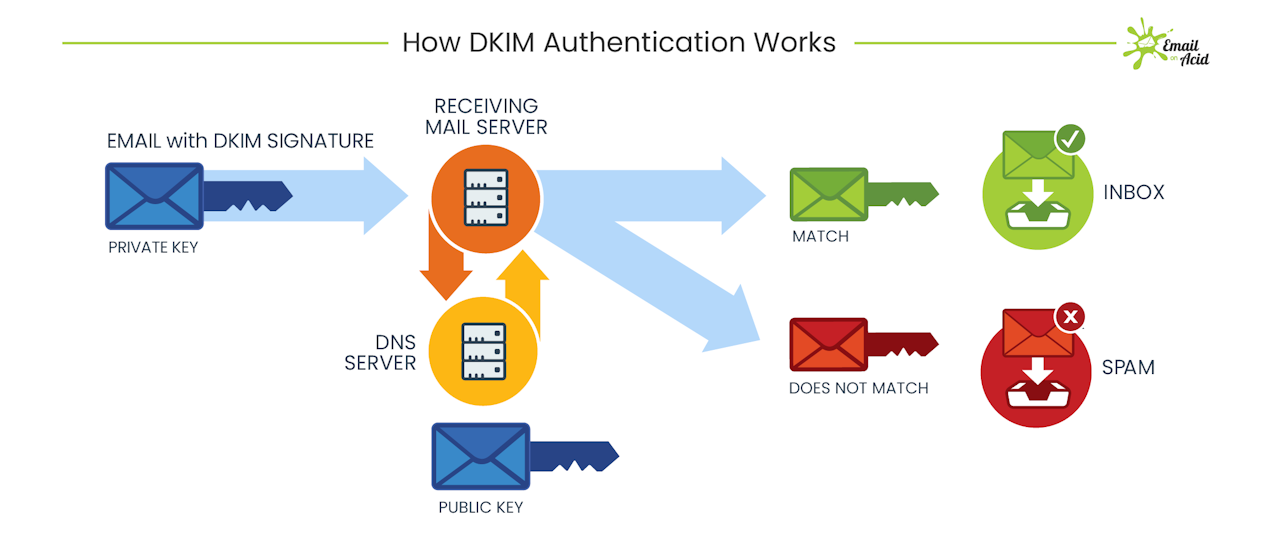
The DomainKeys Identified Mail system uses cryptography to attach an encrypted signature to each email that it transmits. This signature, in essence, validates that the email was not altered or forged in any way in transit.
Domain-based Message Authentication, Reporting & Conformance (DMARC)
While SPF and DKIM tell ESPs how to check if an email sender is authentic, the Domain-based Message Authentication, Reporting & Conformance (DMARC system) is designed to give domain owners agency over how recipients should handle their emails and what they should do with an email claiming to be from them that failed the authentication process.
The DMARC system allows email senders to make policies published in the DNS around how recipients should authenticate their emails and how to process any messages that do not pass the specified checks (e.g., approve, quarantine, or reject).
In order for an email to pass through the DMARC framework, it must also pass through either SPF or DKIM.
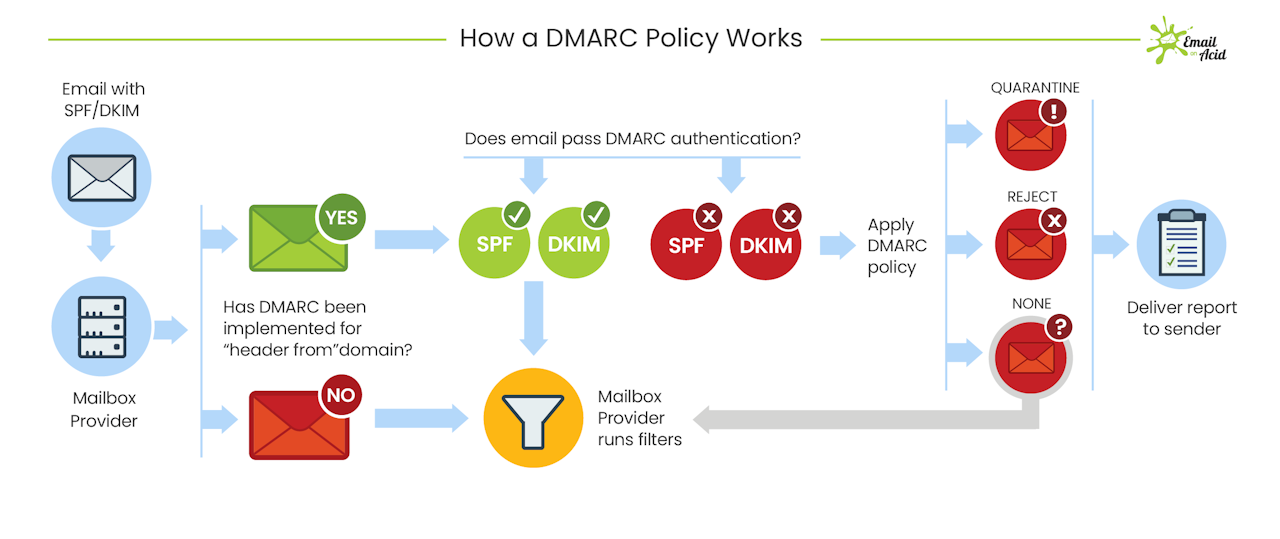
DMARC is very effective in combating spoofing, in which emails are sent pretending to be from you but are actually from someone with malicious intent.
The DMARC system provides a feedback loop to email senders so they can monitor whether the emails that are supposedly being sent from their domains are passing validation checks.
How to Authenticate Your Email
Although the steps for authenticating your email are technical, they’re straightforward and highly executable (if not by your sales team members, then certainly by another tech-savvy member of your organization). 
1. Authenticate Your IP Addresses With SPF
The first step in validating your email is to authenticate your list of IP addresses with the Sender Policy Framework.
You’ll need an individual SPF record for each email domain you plan to use. This ensures that when you send an email from your ESP, the recipient will find that the sender’s IP matches an authorized IP listed in the DNS.
2. Configure DKIM Signatures for Your Messages
The exact process for setting up your DKIM settings will depend on your unique email service provider. Ask the customer service team at your service provider for more details about how to set up this cryptography authentication.
Remember, DKIM helps email recipients feel safe that their incoming messages haven’t been interfered with en route to their inbox.
3. Protect Your Domain With DMARC Authentication
Setting up DMARC gives you peace of mind that any emails that fail SPF and/or DKIM will still avoid harming anyone on your contact list.
DMARC forensic reporting can give sales and marketing teams insight into their deliverability results, issues with failed messages, and how the domain is generally perceived by ESPs.
4. Get Ahead With BIMI
Many organizations are now also expecting a fourth authentication standard called BIMI (Brand Indicators for Message Identification). BIMI is always used in addition to SPF, DKIM, and DMARC — never in place of.
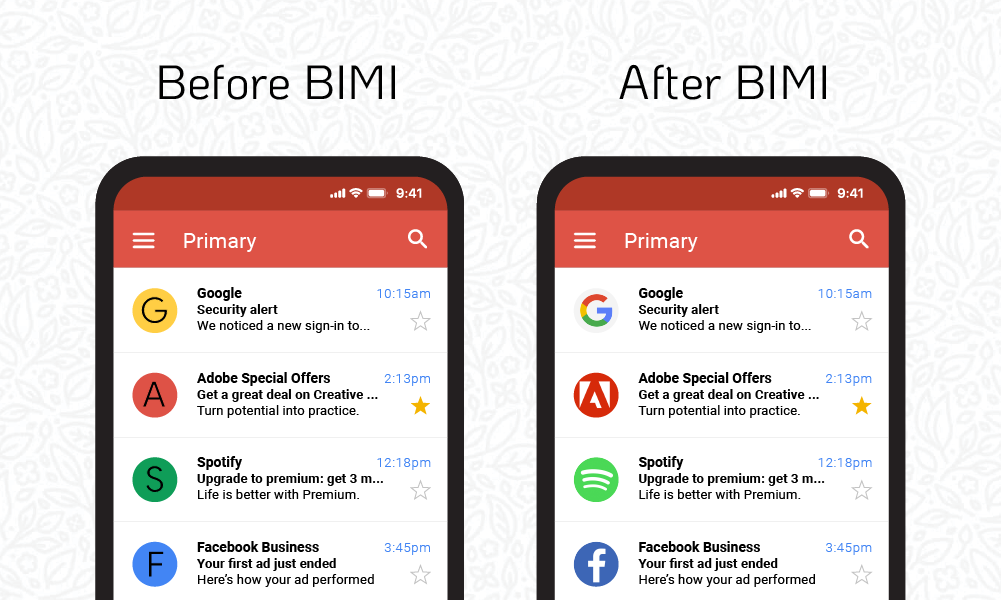
For email senders with a strong reputation of sending trustworthy, credible messages, DMARC in place, and a BIMI record, the Brand Indicator displays an organization’s logo directly in the recipient’s inbox. This is a strong visual trust cue and helps recipients clearly identify your brand.
Tip: Once you’re done authenticating your email, grab some of our ready-to-use sales email templates below.
 18 Proven Email Templates for SalesWinning email templates for cold outreach, follow-ups, and nurturing relationships – backed by data and real-world examples.
18 Proven Email Templates for SalesWinning email templates for cold outreach, follow-ups, and nurturing relationships – backed by data and real-world examples.
Email Authentication Best Practices
Here are some best practices to keep in mind as you navigate email authentication.
Define Technical Standards
No matter how technically savvy your team is (or is not), it’s important that everyone has at least a basic understanding of email security, specifically how it pertains to email authentication.
Ill-intentioned email scammers are constantly looking for ways to stay one step ahead of security systems and validation checks, so it’s important that everyone is on the same page about how to define the rules for email authentication and the training, practices, and expectations around the topic.
Use Consistent Sender Addresses
To the best of your ability, try to send all of your emails from a consistent sender address. This also includes your friendly “From” name that shows up in your recipient’s inbox.
Don’t send emails from “John Smith” and “John S.,” for example — even to different recipients.
Email service providers love senders who are reliable, predictable, recognizable, and consistent.
Never Send From Unregistered Domains
To that end, if you have to send messages from multiple domains, it’s imperative that you confirm that each and every one is configured for SPF and DKIM validations.
Monitor Your Deliverability
Anyone can go in and manually check their SPF and DKIM authentications. They can be found in the email header.
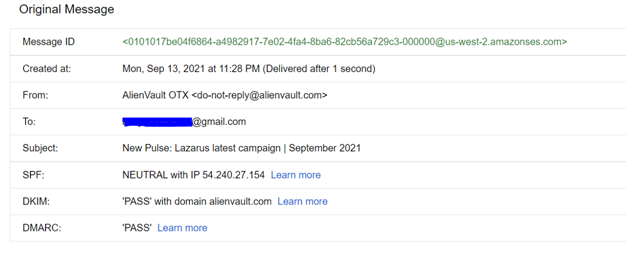
You should monitor these on a regular basis. There are software tools that can help automate and monitor your authentications.
Pay Attention to Details
It’s important to note that email authentication isn’t the kind of thing that can be done partially or imperfectly. “Good enough” can actually be detrimental, as some ESPs see improperly configured email authentication as a red flag for malicious intent.
Make sure you take the time to set it up properly and keep a consistent eye on it.
Have you ever looked into the details of email authentication? Who handles this for your team? Have you ever been on the receiving end of an email with malware?
Get sales tips and strategies delivered straight to your inbox.
Yesware will help you generate more sales right from your inbox. Try our Outlook add-on or Gmail Chrome extension for free, forever!
Related Articles
Jenny Keohane
Jenny Keohane
Melissa Williams
Sales, deal management, and communication tips for your inbox

